For programmers to need to analyze windows event logs by python,this tested source code is useful.
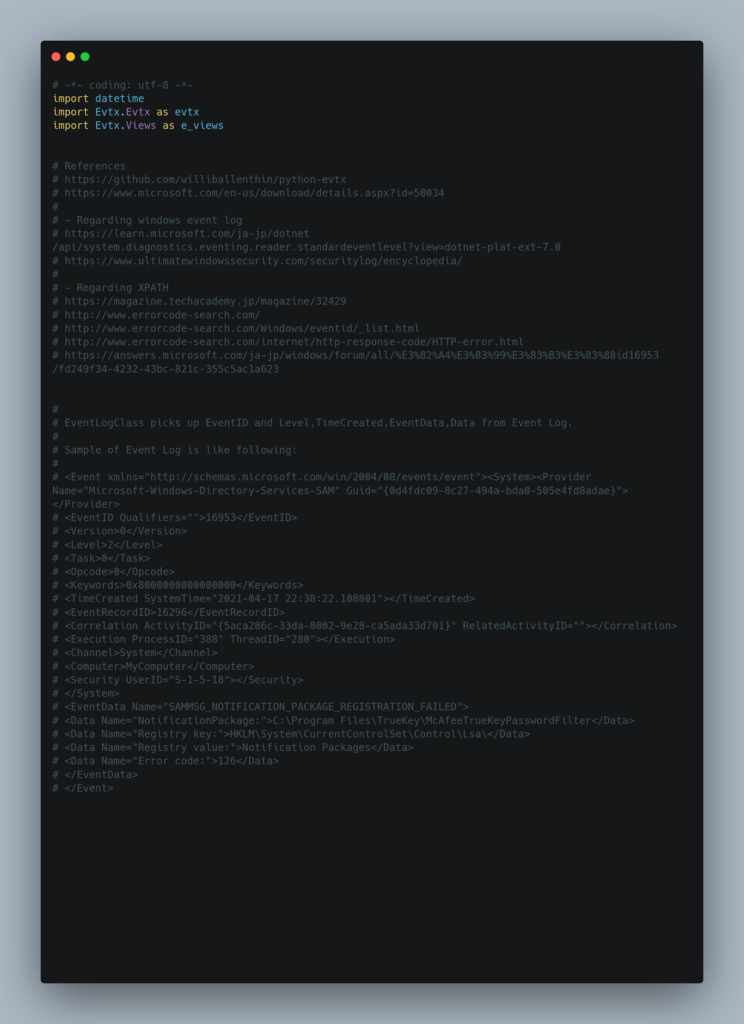
Output is python dictionary format selecting from picks up EventID and Level,TimeCreated,EventData,Data from Event Log.
Output sample is following.
{‘EventID’: ‘4624’, ‘EventID_Qualifiers’: ”, ‘EventID_detail’: ‘An account was successfully logged on’, ‘Level’: ‘0’, ‘Level_detail’: ‘LogAlways : This value indicates that not filtering on the level is done during the event publishing.’, ‘SystemTime’: ‘2023-03-06 08:44:59.487074’, ‘SystemTime_datetimeobj’: datetime.datetime(2023, 3, 6, 8, 44, 59, 487074), ‘EventData’: [], ‘SubjectUserSid’: ‘S-1-5-18’, ‘SubjectUserName’: ‘DESKTOP-UOQP98N$’, ‘SubjectDomainName’: ‘WORKGROUP’, ‘SubjectLogonId’: ‘0x00000000000003e7’, ‘TargetUserSid’: ‘S-1-5-18’, ‘TargetUserName’: ‘SYSTEM’, ‘TargetDomainName’: ‘NT AUTHORITY’, ‘TargetLogonId’: ‘0x00000000000003e7’, ‘LogonType’: ‘5’, ‘LogonProcessName’: ‘Advapi ‘, ‘AuthenticationPackageName’: ‘Negotiate’, ‘WorkstationName’: ‘-‘, ‘LogonGuid’: ‘{00000000-0000-0000-0000-000000000000}’, ‘TransmittedServices’: ‘-‘, ‘LmPackageName’: ‘-‘, ‘KeyLength’: ‘0’, ‘ProcessId’: ‘0x0000000000000148’, ‘ProcessName’: ‘C:\Windows\System32\services.exe’, ‘IpAddress’: ‘-‘, ‘IpPort’: ‘-‘, ‘ImpersonationLevel’: ‘%%1833’, ‘RestrictedAdminMode’: ‘-‘, ‘TargetOutboundUserName’: ‘-‘, ‘TargetOutboundDomainName’: ‘-‘, ‘VirtualAccount’: ‘%%1843’, ‘TargetLinkedLogonId’: ‘0x0000000000000000’, ‘ElevatedToken’: ‘%%1842’}
Specification
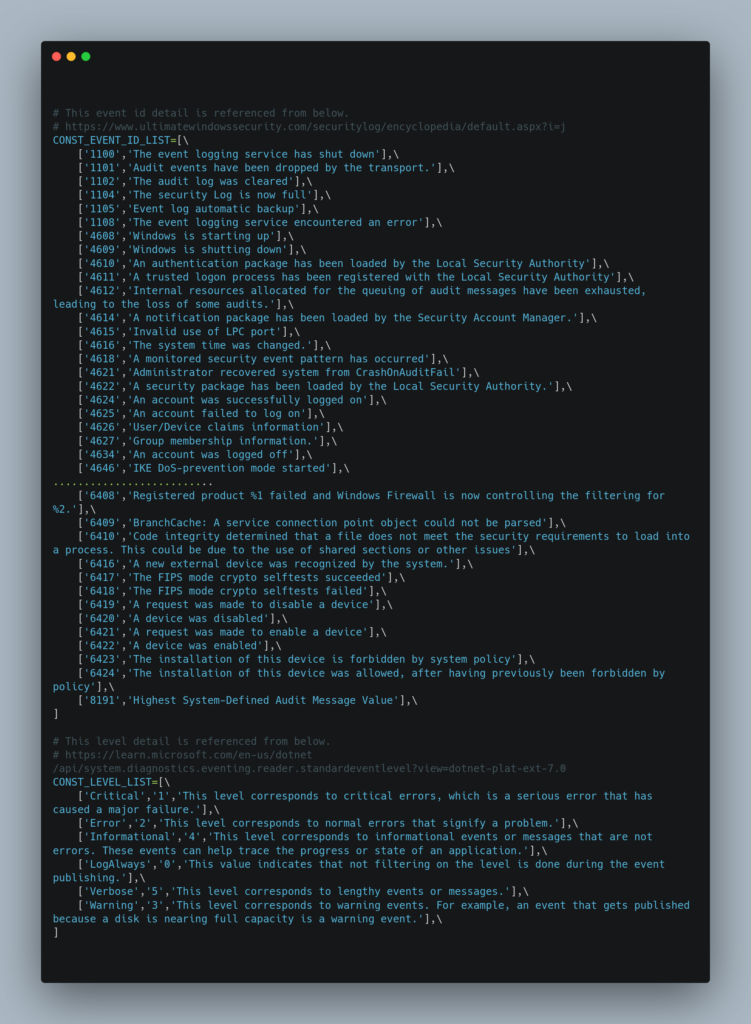
Source Code



Test Result
| NO | test case | result |
| 01 | application log of event log. – analyze application log | OK |
| 02 | security log of event log. – analyze security log | OK |
| 03 | setup log of event log. – analyze setup log | OK |
| 04 | system log of event log. – analyze system log | OK |
Test Code
*) Modify “path” along your PC environment.

History
7/3/2023 created
Provider Profile
Nick name is “Dead Fish” employed as an engineer in Japan.
I am grad if you need my code.
Thanks !
Download
Get download passwordFollowing files and data are zipped.
├── EventLogClass.py
└── evtlog
├── Application.evtx
├── Security.evtx
├── Setup.evtx
└── System.evtx
Remarks
None


Comments
We’re a group of volunteers and opening a new scheme in our community.
Your website provided us with valuable info to
work on. You have done an impressive job and
our whole community will be thankful to you.