For programmers to need to analyze wireshark log(pcap format) by python,this tested source code is useful. Though this is a wrapper of pyshark , this makes easier than directly using pyshark.
Output is python dictionary format selecting ether and ip ,ipv6, tcp ,tls packets from pcap file.Each dictionary entry has a sniffer timestamp.
Output sample is following.
[
[‘ETH’,
{‘sniff_time_str’: ‘2004-05-13 19:17:07.311224’, ‘sniff_time’: datetime.datetime(2004, 5, 13, 19, 17, 7, 311224), ‘sniff_timestamp’: ‘1084443427.311224000’, ‘dst’: ‘fe:ff:20:00:01:00’, ‘dst_resolved’: ‘fe:ff:20:00:01:00’, ‘dst_oui’: ‘16711456’, ‘addr’: ‘fe:ff:20:00:01:00’, ‘addr_resolved’: ‘fe:ff:20:00:01:00’, ‘addr_oui’: ‘16711456’, ‘addr_oui_resolved’: ‘Xerox Corporation’, ‘dst_lg’: ‘1’, ‘lg’: ‘1’, ‘dst_ig’: ‘0’, ‘ig’: ‘0’, ‘src’: ’00:00:01:00:00:00′, ‘src_resolved’: ’00:00:01:00:00:00′, ‘src_oui’: ‘1’, ‘src_oui_resolved’: ‘Xerox Corporation’, ‘src_lg’: ‘0’, ‘type’: ‘0x00000800’}],
[‘IP’,
{‘sniff_time_str’: ‘2004-05-13 19:17:07.311224’, ‘sniff_time’: datetime.datetime(2004, 5, 13, 19, 17, 7, 311224), ‘sniff_timestamp’: ‘1084443427.311224000’, ‘version’: ‘4’, ‘hdr_len’: ’20’, ‘dsfield’: ‘0x00000000’, ‘dsfield_dscp’: ‘0’, ‘dsfield_ecn’: ‘0’, ‘len’: ’48’, ‘id’: ‘0x00000f41’, ‘flags’: ‘0x00004000’, ‘flags_rb’: ‘0’, ‘flags_df’: ‘1’, ‘flags_mf’: ‘0’, ‘frag_offset’: ‘0’, ‘ttl’: ‘128’, ‘proto’: ‘6’, ‘checksum’: ‘0x000091eb’, ‘checksum_status’: ‘2’, ‘src’: ‘145.254.160.237’, ‘addr’: ‘145.254.160.237’, ‘src_host’: ‘145.254.160.237’, ‘host’: ‘145.254.160.237’, ‘dst’: ‘65.208.228.223’, ‘dst_host’: ‘65.208.228.223’}],
[‘IPV6’,
{‘sniff_time_str’: ‘2015-01-03 06:52:36.799722’, ‘sniff_time’: datetime.datetime(2015, 1, 3, 6, 52, 36, 799722), ‘sniff_timestamp’: ‘1420235556.799722000’, ‘version’: ‘6’, ‘ip_version’: ‘6’, ‘tclass’: ‘0x00000000’, ‘tclass_dscp’: ‘0’, ‘tclass_ecn’: ‘0’, ‘flow’: ‘0x00000000’, ‘plen’: ’56’, ‘nxt’: ‘0’, ‘hlim’: ‘1’, ‘src’: ‘fe80::a00:27ff:fed4:10bb’, ‘addr’: ‘fe80::a00:27ff:fed4:10bb’, ‘src_host’: ‘fe80::a00:27ff:fed4:10bb’, ‘host’: ‘fe80::a00:27ff:fed4:10bb’, ‘dst’: ‘ff02::16’, ‘dst_host’: ‘ff02::16’}],
[‘TCP’,
{‘sniff_time_str’: ‘2004-05-13 19:17:07.311224’, ‘sniff_time’: datetime.datetime(2004, 5, 13, 19, 17, 7, 311224), ‘sniff_timestamp’: ‘1084443427.311224000’, ‘srcport’: ‘3372’, ‘dstport’: ’80’, ‘port’: ‘3372’, ‘stream’: ‘0’, ‘len’: ‘0’, ‘seq’: ‘0’, ‘seq_raw’: ‘951057939’, ‘nxtseq’: ‘1’, ‘ack’: ‘0’, ‘ack_raw’: ‘0’, ‘hdr_len’: ’28’, ‘flags’: ‘0x00000002’, ‘flags_res’: ‘0’, ‘flags_ns’: ‘0’, ‘flags_cwr’: ‘0’, ‘flags_ecn’: ‘0’, ‘flags_urg’: ‘0’, ‘flags_ack’: ‘0’, ‘flags_push’: ‘0’, ‘flags_reset’: ‘0’, ‘flags_syn’: ‘1’, ‘flags_fin’: ‘0’, ‘flags_str’: ‘\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7\xc2\xb7S\xc2\xb7’, ‘window_size_value’: ‘8760’, ‘window_size’: ‘8760’, ‘checksum’: ‘0x0000c30c’, ‘checksum_status’: ‘2’, ‘urgent_pointer’: ‘0’, ‘time_relative’: ‘0.000000000’, ‘time_delta’: ‘0.000000000’, ‘retransmit’: False}],
[‘TLS’,
{‘sniff_time_str’: ‘2020-11-11 06:06:14.511243’, ‘sniff_time’: datetime.datetime(2020, 11, 11, 6, 6, 14, 511243), ‘sniff_timestamp’: ‘1605042374.511243000’, ‘record’: ‘TLSv1.2 Record Layer: Handshake Protocol: Client Hello’, ‘record_content_type’: ’22’, ‘record_version’: ‘0x00000303’, ‘record_length’: ‘182’}]
]
Specification
| ID | STCD_0000000009 |
| Language | Python |
| Steps | 288 |
| Purpose | Analyze wireshark log (pcap format) . |
| Function | Analyze wireshark log (pcap format) by using pyshark. |
| Environment | Ubuntu 20.04.4 LTS Anaconda3(Python 3.9.7) IDE : Visual Studio Code pyshark tshark wireshark |
| Restriction | free license You can use source code copy as owner . You can customize and distribute it freely. |
| Price | 7 dollars or 700 yen (Pay with PayPal) |
| References | https://github.com/KimiNewt/pyshark https://pypi.org/project/pyshark/ https://lindevs.com/install-tshark-on-ubuntu https://askubuntu.com/questions/436203/how-do-i-get-the-pcap-lib-on-ubuntu https://linuxhint.com/install_wireshark_ubuntu/ |
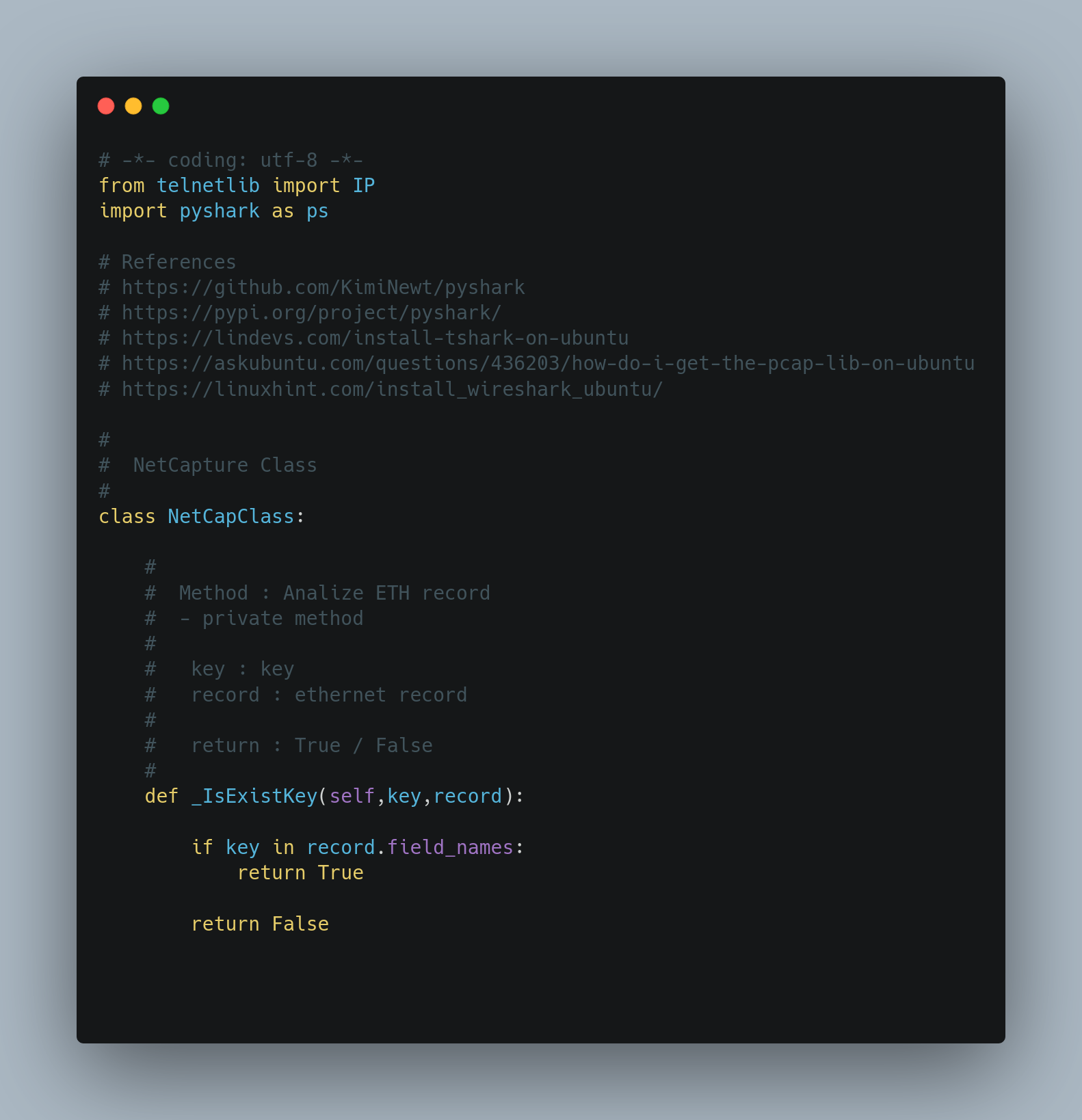
Source Code
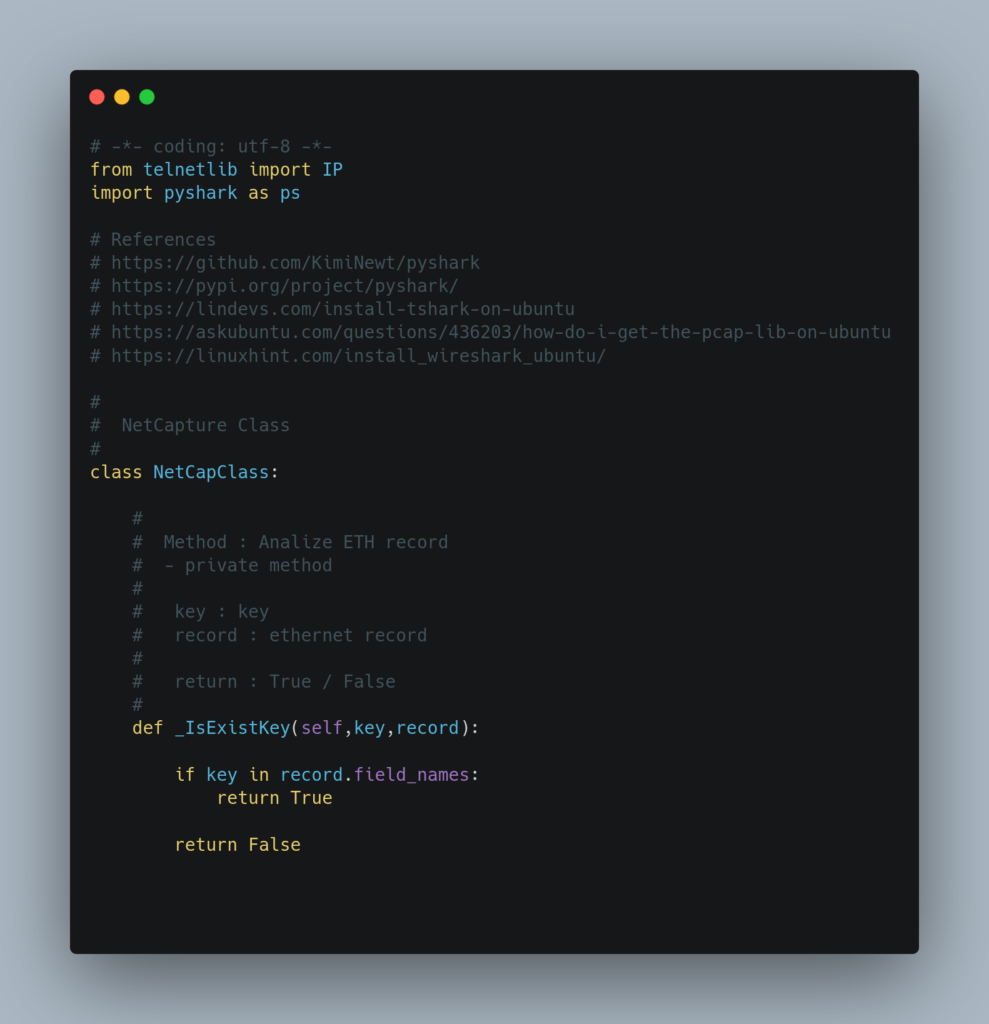
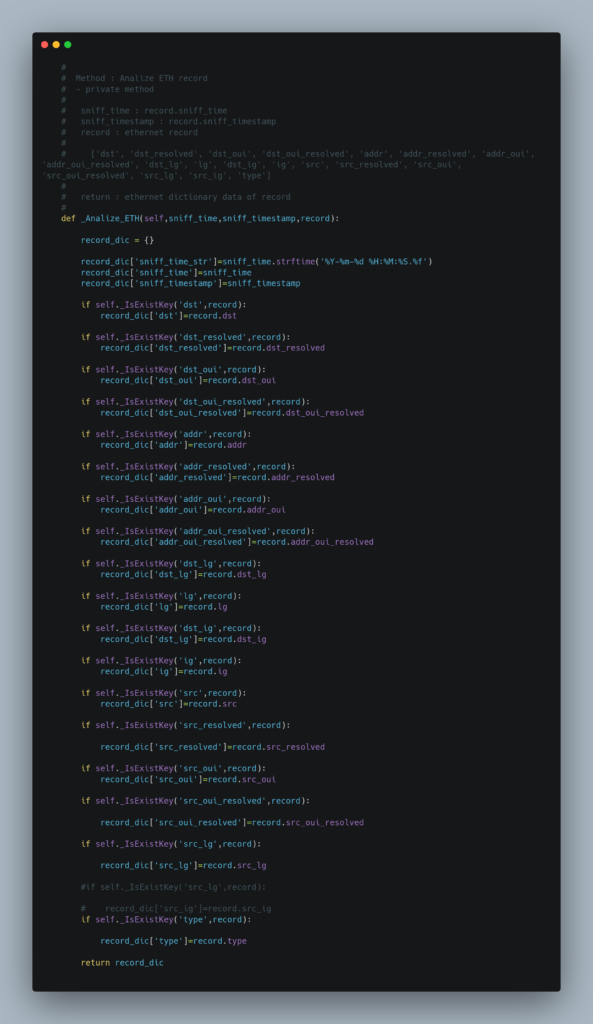

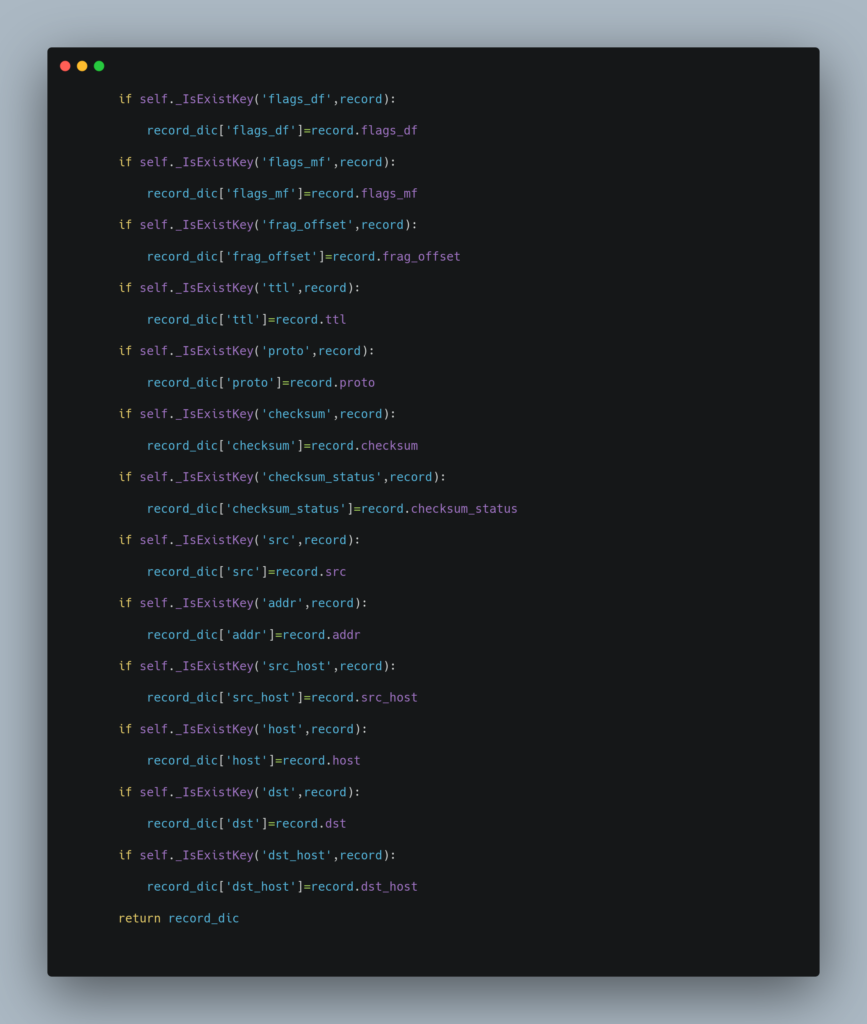
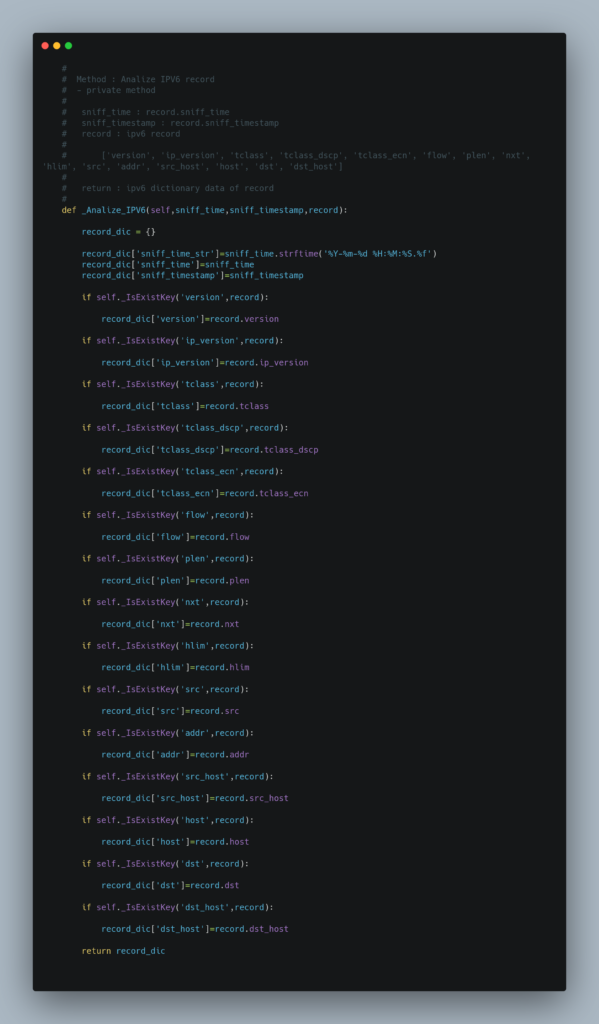
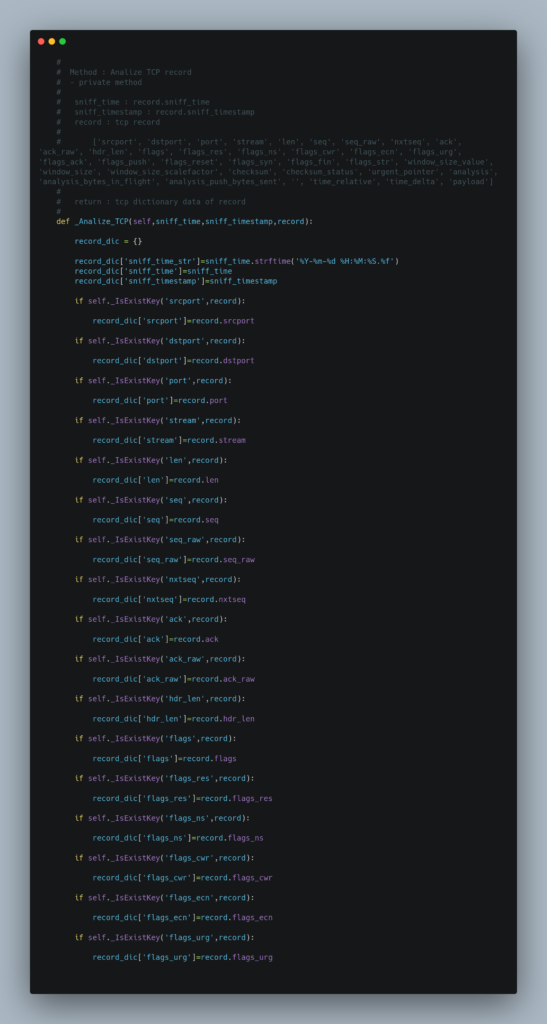
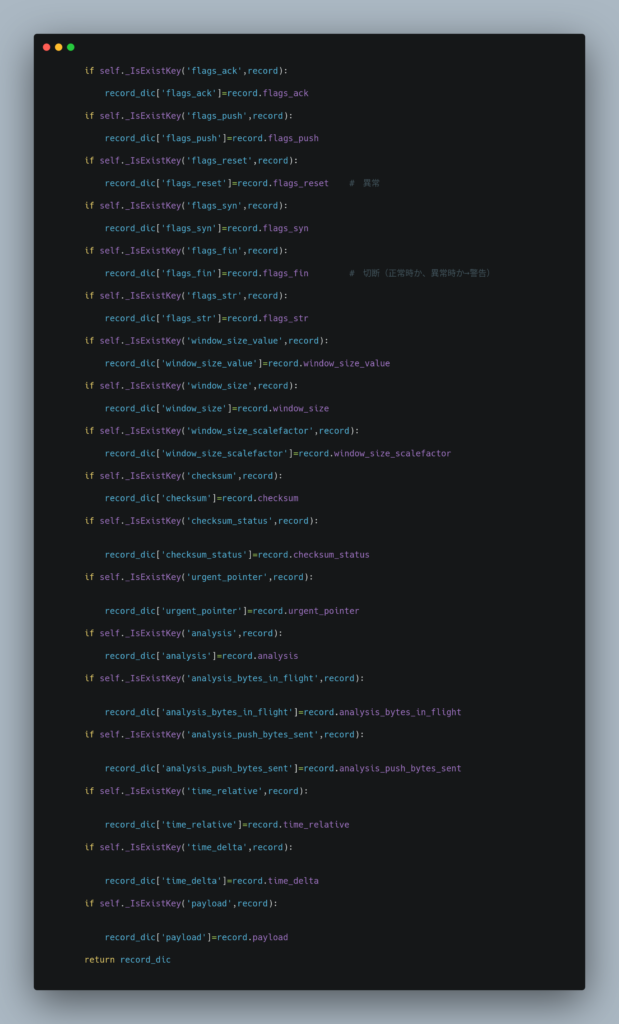
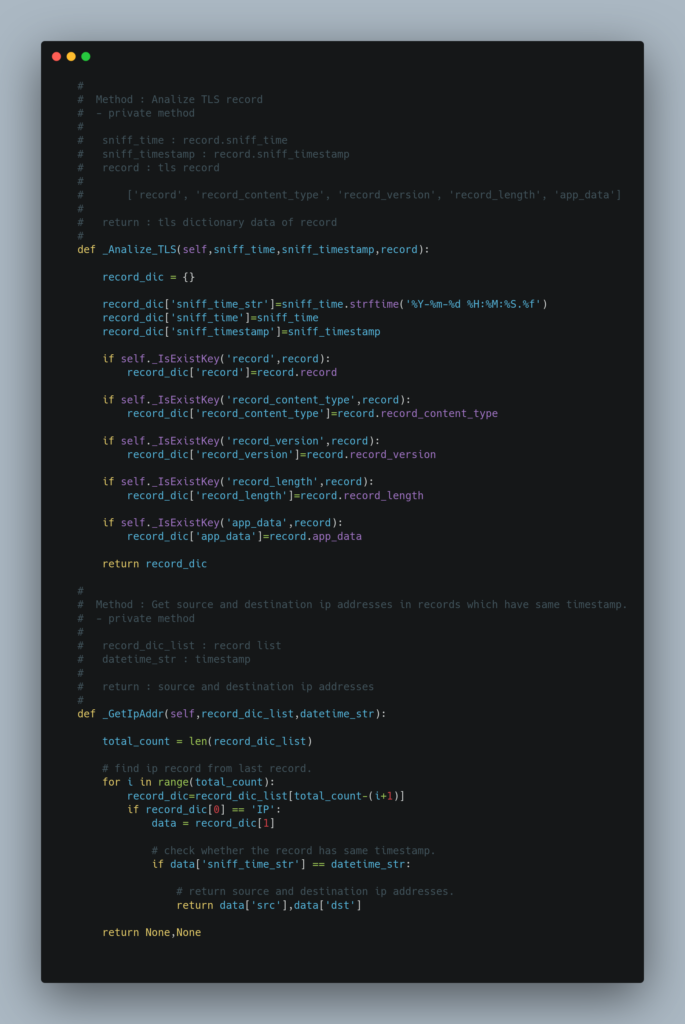

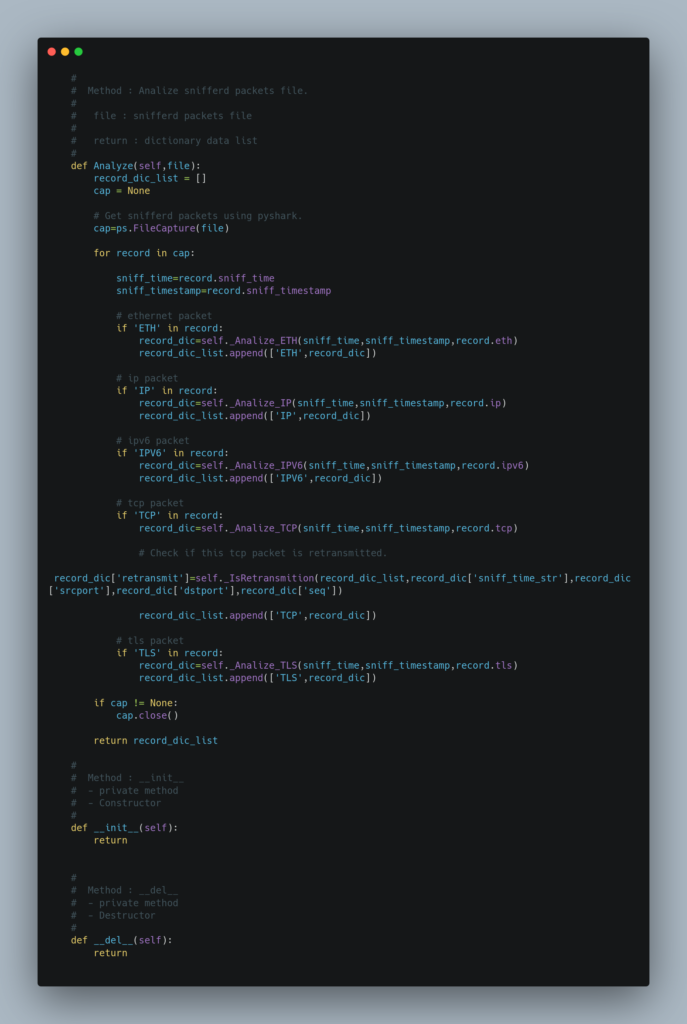
Test Result
| NO | test case | result |
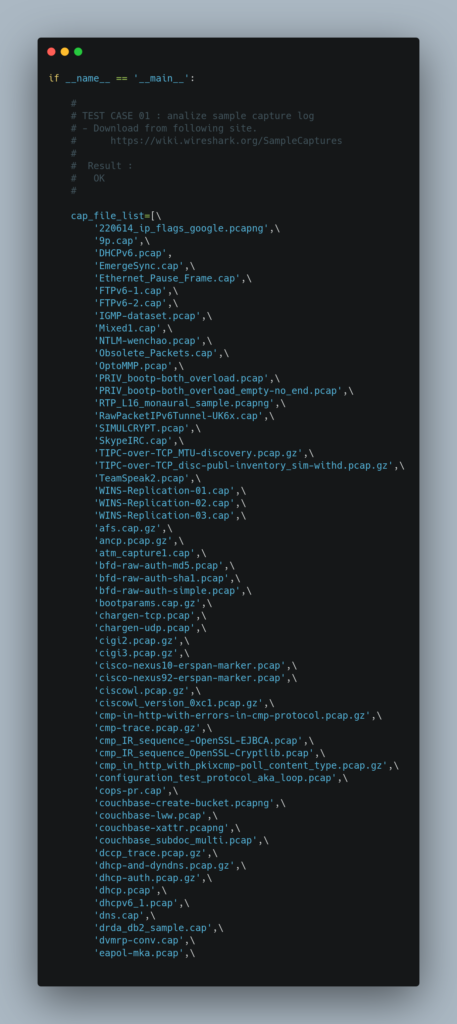
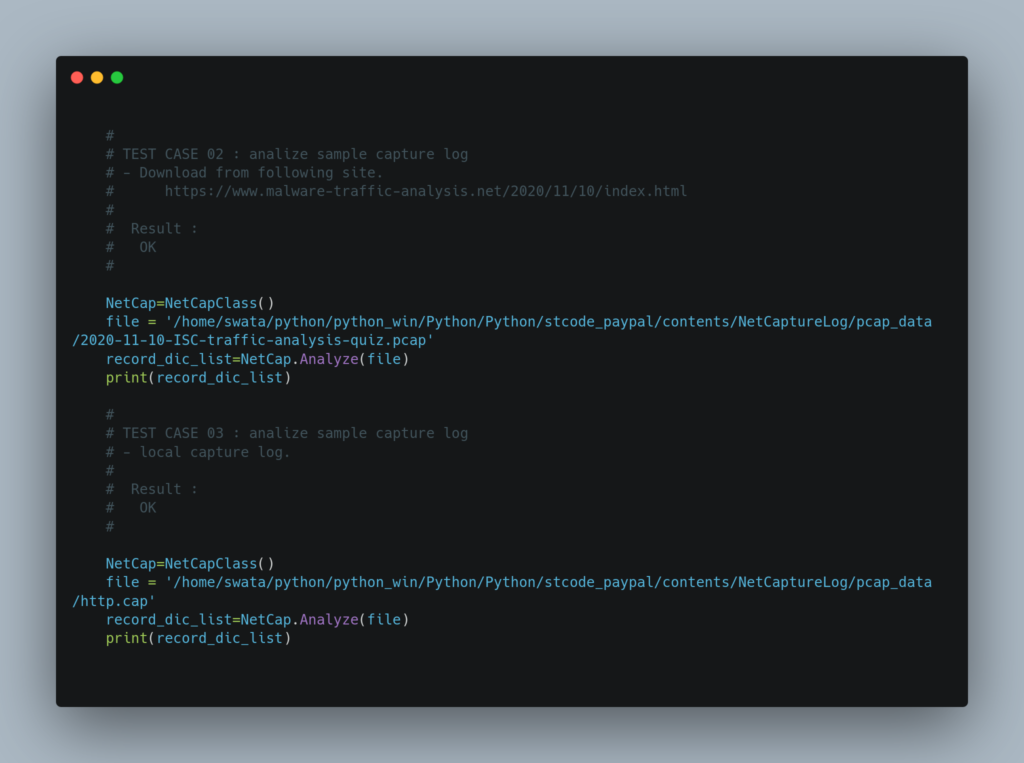
| 01 | Analyze sample capture log. – Download from following site. https://wiki.wireshark.org/SampleCaptures | OK |
| 02 | Analyze sample capture log. – Download from following site. https://www.malware-traffic-analysis.net/2020/11/10/index.html | OK |
| 03 | Analyze sample capture log – local capture log. | OK |
Test Code
*) Modify “path” along your PC environment.

History
4/3/2023 created
Provider Profile
Nick name is “Dead Fish” employed as an engineer in Japan.
I am grad if you need my code.
Thanks !
Download
Get download passwordFollowing files and data are zipped.
├── NetCapClass.py
└── pcap_data
├── 2020-11-10-ISC-traffic-analysis-quiz.pcap
├── SampleCaptures
│ ├── 220614_ip_flags_google.pcapng
│ ├── 9p.cap
│ ├── Apple_IP-over-IEEE_1394_Packet.pcap
│ ├── BT_USB_LinCooked_Eth_80211_RT.ntar.gz
│ ├── DHCPv6.pcap
│ ├── EmergeSync.cap
│ ├── Ether-S-IO_traffic_01.pcap.gz
│ ├── Ethernet_Pause_Frame.cap
│ ├── FTPv6-1.cap
│ ├── FTPv6-2.cap
│ ├── IGMP-dataset.pcap
│ ├── IrDA_Traffic.ntar
│ ├── Mixed1.cap
│ ├── NTLM-wenchao.pcap
│ ├── Obsolete_Packets.cap
│ ├── OptoMMP.pcap
│ ├── PRIV_bootp-both_overload.pcap
│ ├── PRIV_bootp-both_overload_empty-no_end.pcap
│ ├── Public_nic
│ ├── RTP_L16_monaural_sample(1).pcapng
│ ├── RTP_L16_monaural_sample.pcapng
│ ├── RawPacketIPv6Tunnel-UK6x.cap
│ ├── SIMULCRYPT.pcap
│ ├── SITA-Protocols.cap
│ ├── SkypeIRC.cap
│ ├── TIPC-over-TCP_MTU-discovery.pcap.gz
│ ├── TIPC-over-TCP_disc-publ-inventory_sim-withd.pcap.gz
│ ├── TeamSpeak2.pcap
│ ├── WINS-Replication-01.cap
│ ├── WINS-Replication-02.cap
│ ├── WINS-Replication-03.cap
│ ├── afs.dat
│ ├── ancp.pcap.gz
│ ├── atm_capture1.cap
│ ├── bacnet-arcnet.cap
│ ├── bfd-raw-auth-md5.pcap
│ ├── bfd-raw-auth-sha1.pcap
│ ├── bfd-raw-auth-simple.pcap
│ ├── bootparams.dat
│ ├── chargen-tcp.pcap
│ ├── chargen-udp.pcap
│ ├── cigi2.pcap.gz
│ ├── cigi3.pcap.gz
│ ├── cisco-nexus10-erspan-marker.pcap
│ ├── cisco-nexus92-erspan-marker.pcap
│ ├── ciscowl.pcap.gz
│ ├── ciscowl_version_0xc1.pcap.gz
│ ├── cmp-in-http-with-errors-in-cmp-protocol.pcap.gz
│ ├── cmp-trace.pcap.gz
│ ├── cmp_IR_sequence_-OpenSSL-EJBCA.pcap
│ ├── cmp_IR_sequence_OpenSSL-Cryptlib.pcap
│ ├── cmp_in_http_with_pkixcmp-poll_content_type.pcap.gz
│ ├── configuration_test_protocol_aka_loop.pcap
│ ├── cops-pr.cap
│ ├── couchbase-create-bucket.pcapng
│ ├── couchbase-lww.pcap
│ ├── couchbase-xattr.pcapng
│ ├── couchbase_subdoc_multi.pcap
│ ├── data
│ ├── dccp_trace.pcap.gz
│ ├── dhcp-and-dyndns.pcap.gz
│ ├── dhcp-auth.pcap.gz
│ ├── dhcp.pcap
│ ├── dhcpv6_1.pcap
│ ├── dns.cap
│ ├── drda_db2_sample.cap
│ ├── dualhome.iptrace
│ ├── dvmrp-conv.cap
│ ├── eapol-mka.pcap
│ ├── ecpri.pcap
│ ├── epmd.pcap
│ ├── exablaze_trailer.pcap
│ ├── exec-sample.pcap
│ ├── fw1_mon2018.cap
│ ├── genbroad.snoop
│ ├── gryphon.cap
│ ├── hart_ip.pcap
│ ├── hsrp-and-ospf-in-LAN
│ ├── hsrp.pcap
│ ├── ieee802154-association-data.pcap.gz
│ ├── imap.cap
│ ├── iperf3-udp.pcapng.gz
│ ├── ipp.pcap
│ ├── ipv4_cipso_option.pcap
│ ├── ipv4frags.pcap
│ ├── iseries.cap
│ ├── isl-2-dot1q.cap
│ ├── lacp1.pcap
│ ├── lacp1.pcap.gz
│ ├── linx-setup-pingpong-shutdown.pcap
│ ├── llrp.cap
│ ├── llt-sample.pcap
│ ├── lustre-lnet_sample.cap
│ ├── macsec_cisco_trunk.pcap
│ ├── messenger.pcap
│ ├── mms.pcap.gz
│ ├── monotone-netsync.cap
│ ├── mpeg2_mp2t_with_cc_drop01.pcap
│ ├── mpls-basic.cap
│ ├── mpls-exp.cap
│ ├── mpls-te.cap
│ ├── mpls-twolevel.cap
│ ├── msnms.pcap
│ ├── netbench_1.cap
│ ├── openwire_sample.pcap
│ ├── pana-draft18.cap
│ ├── pana-rfc5191.cap
│ ├── pana.cap
│ ├── pim-reg.cap
│ ├── ptpv2.pcap
│ ├── ptpv2_anon.pcapng
│ ├── rpl-dio-mc-nsa-optional-tlv-dissector-sample.pcap
│ ├── rpl_sample.cap
│ ├── rsvp-PATH-RESV.pcap
│ ├── rtmp_sample.cap
│ ├── rtps_cooked(1).pcapng
│ ├── rtps_cooked.pcapng
│ ├── sbus.pcap
│ ├── starteam_sample.cap
│ ├── tfp_capture.pcapng
│ ├── tipc-bundler-messages.pcap
│ ├── tipc-publication-payload-withdrawal.pcap
│ ├── tipc_v2_fragmenter_messages.pcap.gz
│ ├── ultimate_wireshark_protocols_pcap_220213.pcap
│ ├── uma_ho_req_bug.cap
│ ├── unistim-call.pcap
│ ├── unistim_phone_startup.pcap
│ ├── v6-http.cap
│ ├── v6.pcap
│ ├── vlan.cap
│ ├── vnc-sample.pcap
│ ├── vxi-11.pcap.gz
│ ├── wol.pcap
│ ├── wpsdata.cap
│ ├── yami.pcap
│ └── zigbee-join-authenticate.pcap.gz
└── http.cap
Remarks
None


Comments
Hello, the whole thing is going perfectly here and ofcourse every one is sharing
information, that’s genuinely fine, keep up writing.